How do you stop risky sessions without tanking productivity?
That’s the challenge most IT and security teams face as work moves outside controlled office networks. Devices, users, and connections constantly change, making traditional access controls too rigid or too lenient.

This is where Extended Access Policies (XAP) come in. They add an adaptive layer of security that checks user, device, and environment context before granting or maintaining access. By continuously verifying posture and risk, XAP keeps sessions safe, not just at login but throughout their lifecycle.
This guide walks you through what XAP is, why it’s essential for a Zero Trust setup, and how you can easily configure it using Scalefusion OneIdP. It’s built for identity engineers, security architects, and IT admins who want to move beyond static rules toward smarter, context-driven access.
What are Extended Access Policies (XAP)?
Extended Access Policies are intelligent, context-aware access controls that go beyond basic authentication. Instead of granting access purely based on credentials, XAP evaluates a mix of factors such as:
- User identity and role
- Device posture (security tools installed, OS version, encryption status)
- Network and location context
- Behavioral signals (unusual access times, impossible travel, or new device)
Unlike one-time verification methods, XAP applies continuous checks during sessions. This aligns perfectly with Zero Trust principles — never trust, always verify. It ensures access remains valid only as long as risk signals stay within acceptable limits.
Why Extended Access Policies matter?
Static access policies were designed for a world where users worked inside corporate offices on managed devices. That world no longer exists. Today, users sign in from airports, home networks, co-working spaces, and public cafés — all with different risk profiles.
Extended Access Policies help organizations adapt to this dynamic environment by adding intelligence to authentication decisions. For instance, imagine a remote employee connecting from a café’s public Wi-Fi. Everything seems fine until the system detects the device is missing endpoint protection or behaving abnormally. Instead of allowing full access, XAP can trigger additional verification or limit the session scope automatically.
A real scenario might look like this:
- Remote worker connecting from public Wi-Fi
- Device missing security tools
- Behavioral anomaly detected
- Step-up MFA triggered automatically
XAP doesn’t rely on fixed assumptions about networks or locations. It constantly evaluates posture and context, helping organizations maintain both productivity and strong security.
How Extended Access Policies (XAP) work?
Here’s an overall view of how the process works:
Policy Definition
An administrator defines access conditions within the Scalefusion portal using the XAP configuration wizard. These conditions may include compliance status, OS updates and patches, IP address, device location, installed applications, and other contextual signals.
Real-Time Evaluation
Scalefusion evaluates these conditions in real time using its built-in Rules Engine, continuously monitoring device posture and user context against the defined policies.
Signal Transmission to OneIdP
Based on the evaluation, Scalefusion passes a compliance signal to OneIdP, indicating whether the device and user meet the defined access criteria.
Access Enforcement by OneIdP
OneIdP uses this compliance signal to:
- Allow or block access to SSO-integrated services
- Automatically log out users from devices that no longer meet compliance requirements
- Store logs and audit data for future analysis and compliance reporting
This continuous loop between Scalefusion and OneIdP ensures every access request is validated through real-time context, helping organizations maintain Zero Trust enforcement without manual intervention.
How to set up XAP in OneIdP?
You can enforce Extended Access Policies directly within Scalefusion OneIdP using its integrated Zero Trust and posture-based access engine.
Follow these steps:
Pre-Requisites
Before you start, make sure these are configured on the Scalefusion Dashboard:
- User Groups are created.
- SSO is configured for the required applications.
- Veltar > Compliance is set up.
- OS Updates & Patch Management is configured.
Step 1: Create Configuration
To create or edit an Extended Access Policy (XAP) configuration,
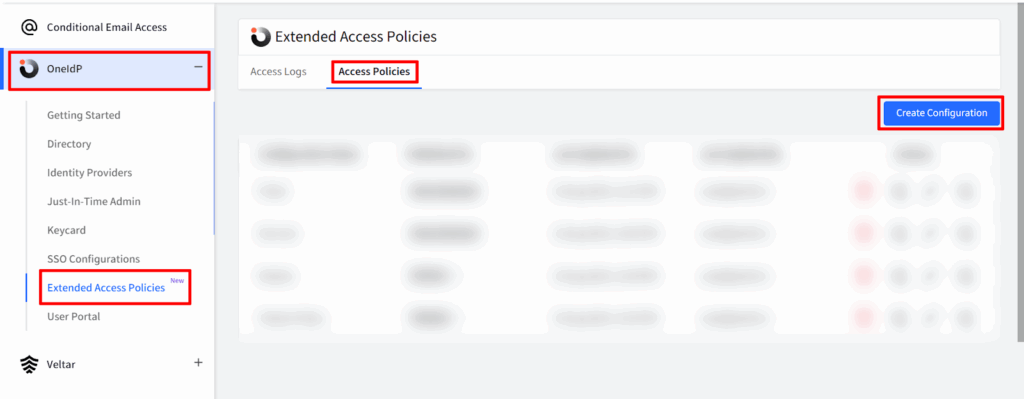
- On Scalefusion Dashboard, navigate to OneIdP > Extended Access Policies > Access Policies
- Click on Create Configuration to open the XAP Wizard.
3. Enter a name for your configuration.
4. Configure the following tabs:
- Compliance & Security – Set access based on Veltar compliance, risk level, or pending OS updates and patches.
- Location – Restrict or allow access using geofence-based rules for managed and unmanaged devices.
- IP Address – Allow logins only from specific IP ranges (public or private).
- Application Status – Require specific apps (and versions) to be installed for access.
- General – Block rooted/jailbroken devices, enforce domain join checks, and define how non-compliant devices are handled.
5. Click Save Configuration when done.
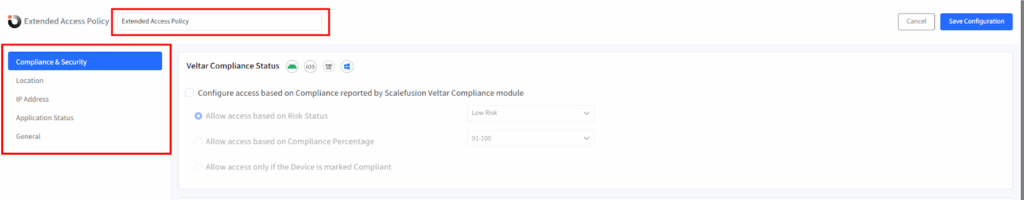
1. Compliance & Security Settings
- Go to the Compliance & Security tab in the XAP Wizard.
- Configure access based on Veltar Compliance and OS update status.
- Choose how access should be controlled:
- Based on Risk Status – Allow devices with selected risk levels (Low, Medium).
- Based on Compliance Percentage – Set the minimum compliance percentage (50–100%) required for access.
- Only if Marked Compliant – Grant access only to devices marked as compliant.
- When Compliance Is Not Reported – Optionally allow access for devices that haven’t yet reported compliance (e.g., during first setup or offline).
- Based on Risk Status – Allow devices with selected risk levels (Low, Medium).
- Click Save after selecting the desired compliance rules.
2. OS Updates & Patches Access Control
| Platform | Conditions |
| Android | No pending OS updates older than [15-30] daysCheck OS Update based on:Update Release DateReported On |
| Linux | No pending critical or security updates;No OS updates older than [15-30] daysCheck OS Update based on:Update Release DateReported On |
| macOS | No pending OS updates older than [15-30] days |
| Windows | No pending critical or security updates;No OS updates older than [15-30] daysCheck OS Update based on:Update Release DateReported On |
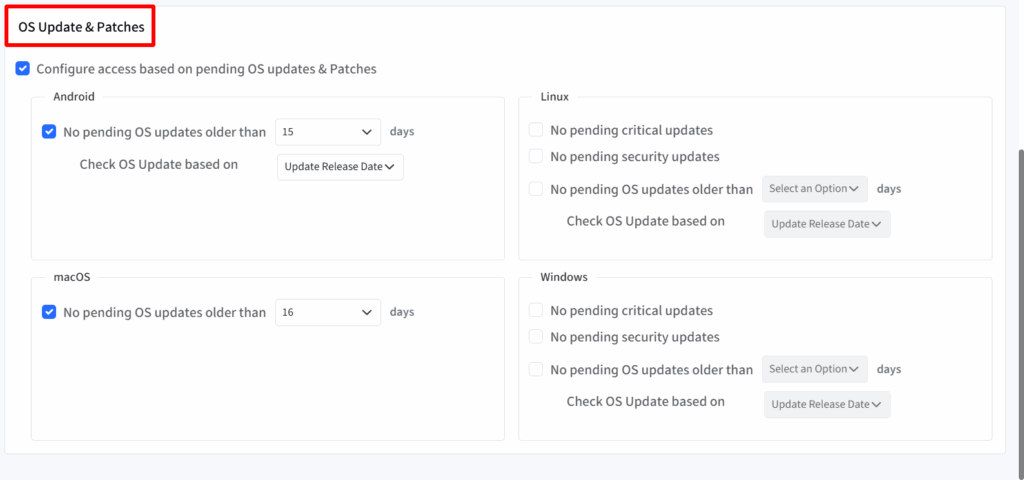
3. Location Settings
- Go to the Location tab to set up location-based access rules using geofences.
- Make sure the geofence is published on managed devices before applying the XAP policy.
- Choose how location control should work:
- Based on Geofence Events (Managed Devices) – Allow or restrict access when a managed device moves in or out of a geofence. You can apply this for Android, iOS/iPadOS, macOS, and Windows.
- Based on Geofence (Unmanaged Devices) – Control browser logins on unmanaged devices using selected geofences from the dashboard.
- Based on Geofence Events (Managed Devices) – Allow or restrict access when a managed device moves in or out of a geofence. You can apply this for Android, iOS/iPadOS, macOS, and Windows.
- Click Save once you’ve set the desired rules.
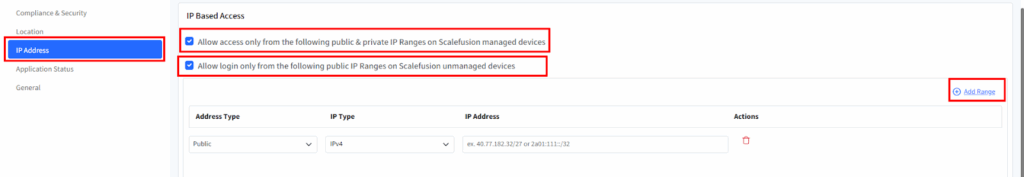
4. IP Address Settings
- Go to the IP Address tab to set up access controls based on IP ranges.
- Choose how you want to apply IP-based restrictions:
- For Managed Devices – Allow access only from specified public or private IP ranges for Scalefusion-managed devices.
- For Unmanaged Devices – Restrict browser logins to selected public IP ranges only.
- For Managed Devices – Allow access only from specified public or private IP ranges for Scalefusion-managed devices.
- Use the IP Address table to add and define allowed IP ranges.
| Field | Description |
| Address Type | Select Public or Private IP addresses |
| IP Type | Choose IPv4 or IPv6 |
| IP Address | Enter valid IP addresses or ranges in CIDR format (e.g., 192.168.1.0/24) |
| Actions | – Add Range: Adds a new row for IP input – Delete: Removes a row |
By clicking on Add Range, you can add multiple IP ranges as needed to cover different network segments.
5. Application Status Settings
- Go to the Application Status tab to set rules based on installed apps and their versions.
- Enable Allow access based on application install status and version.
- Define which apps must be installed on a device to allow access, and optionally set a minimum version for each app.
- Use the Application table to add and manage these rules for different operating systems.
| Field | Description |
| OS | Select the platform:Android,iOS/iPadOS,macOS,Windows |
| Application | Search for the application (searches apps from your account based on the selected OS). Lists all applications installed on the device including Enterprise Apps and Scalefusion Managed Apps. |
| Install Status | Installed |
| Version Check | Choose if and how to validate the app version:Not Required (default)Version Name (e.g., v1.2.3): Exact matchVersion Code (e.g., 10203): Exact matchVersion Name Equal or aboveVersion Code Equal or above |
| Version Info | Enter the version value (enabled only if Version Check is set to Name or Code) |
| Actions | – Delete: Removes a row from the table |
Likewise, click on Add App on the top right to add multiple apps for different OS.

6. General Settings
- Go to the General tab in the Extended Access Policy wizard to configure additional access rules and fallback options.
- Block Access if Device is Jailbroken, Rooted, or Fails Attestation
- Prevents access from devices that are jailbroken (iOS), rooted (Android), or fail attestation checks.
- Applies to: Android, iOS, macOS
- Prevents access from devices that are jailbroken (iOS), rooted (Android), or fail attestation checks.
- Allow Access Only if Devices are Domain Joined
- Grants access only to devices that are domain joined.
- Applies to: Windows
- Grants access only to devices that are domain joined.
- Choose Non-Compliant Handling for Scalefusion Managed Devices
- Decide how to handle access for devices marked as non-compliant:
- Allow users to remediate for self-remediable compliance issues – Users will be prompted to fix the issues themselves.
- Decide how to handle access for devices marked as non-compliant:
- View Details: Displays all failed rule summaries.
- Scan Now: Immediately triggers a compliance scan on desktop devices.
- Update: Starts installing pending OS updates.
- If pending OS updates or patches are detected, a separate message appears.

- Show the Access Denied message configured in SSO – Blocks access and shows the message defined in your SSO configuration.

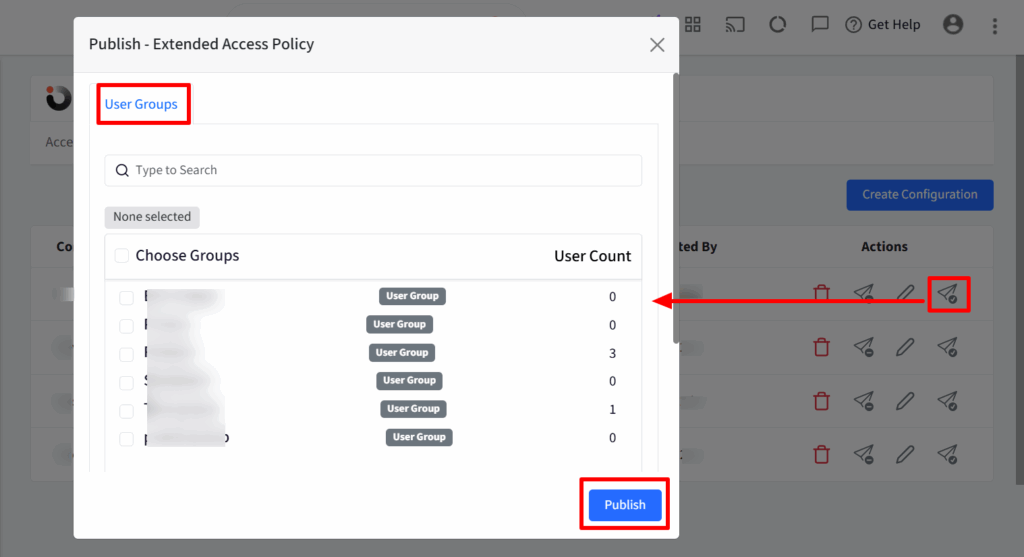
Step 2: Publish Configuration
- After creating the configuration, it will appear under the Access Policies tab.
- Click the Publish icon next to the configuration.
- In the pop-up window, select the user group(s) where you want to apply the configuration.
- Click Publish to complete the process.
Additional Actions
You can manage your existing configurations with the following options:
- Unpublish – Remove the Extended Access Policy from the user groups where it’s applied.
- Edit – Modify the configuration settings as needed.
- Delete – Permanently remove the configuration and clear related compliance records from all associated devices.

End User Experience
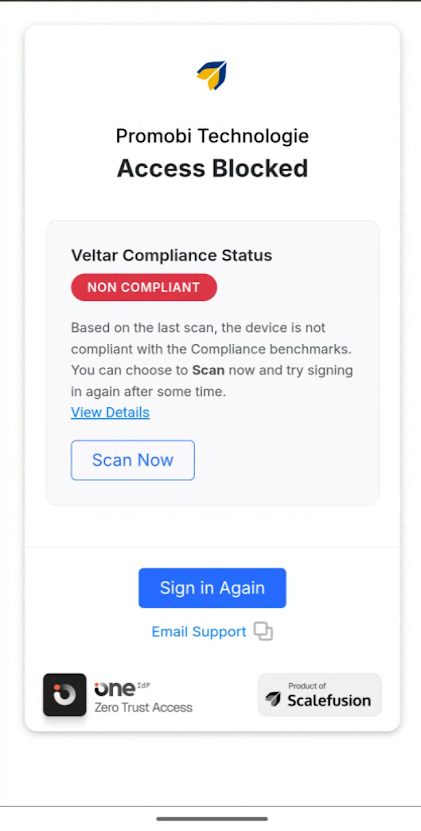
When users sign in on a device with an Extended Access Policy (XAP) applied, they’ll see a compliance check screen during login.
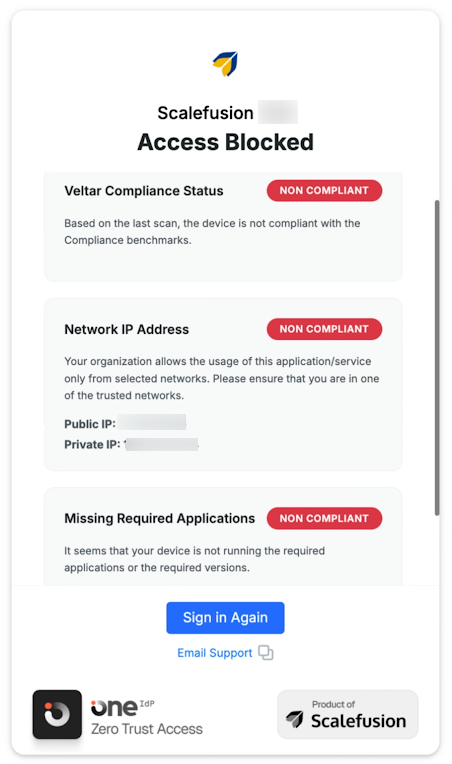
This screen appears when policies such as Veltar Compliance, IP restrictions, or application requirements are active.
Adopt context-aware authentication with Scalefusion OneIdP’s XAP capabilities
Strong, context-aware access security is essential in today’s distributed work environment. Traditional access controls based on network or location can’t keep up with hybrid and remote work patterns. What organizations need is visibility into who is accessing resources, from where, and under what conditions.
That’s exactly what Scalefusion OneIdP’s Extended Access Policies (XAP) deliver.
By combining device posture signals from Scalefusion with identity context in OneIdP, organizations gain a unified access control layer that:
- Reduces exposure from risky sessions
- Ensures only compliant, secure devices can connect
- Detects and responds to anomalies instantly
- Strengthens the foundation of a Zero Trust framework
With OneIdP, access decisions become smarter, faster, and more reliable — giving IT teams the confidence to enforce security without slowing business down.
See how OneIdP can help you enforce smarter access policies.
Schedule a demo now.


